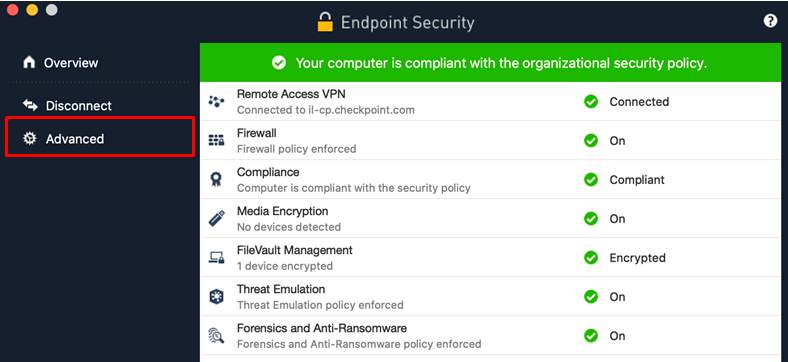
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'EFRService.exe'

PDF) Guide to Computer Forensics and Investigations: Processing Digital Evidence | Abigail Eason - Academia.edu
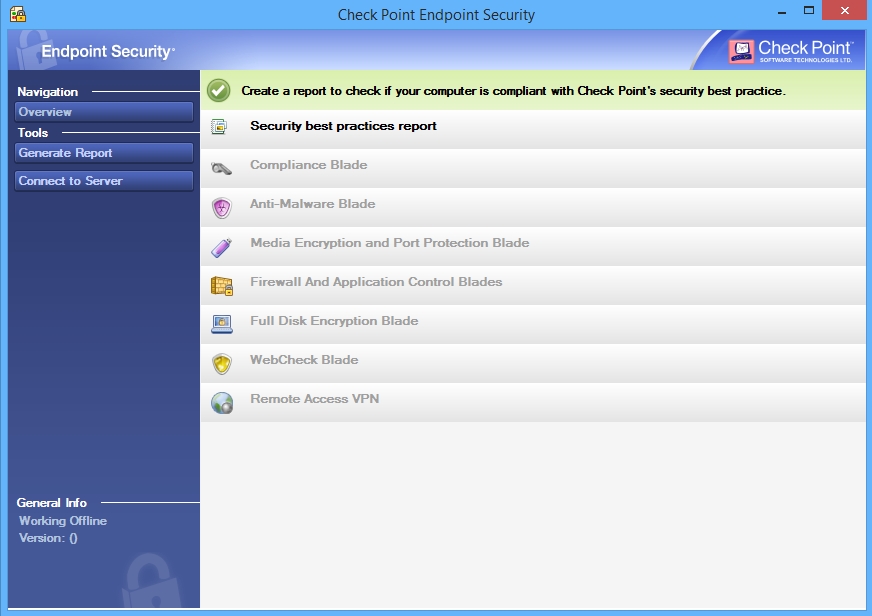
Check Point Endpoint Security Download - The software provides data and network security, advanced threat prevention


.jpg?width=1000&name=Check%20Point%20Harmony%20EDR%20(USE).jpg)

.jpg?width=1000&name=Symantec_Advanced_Threat_Protection_EDR(USE).jpg)

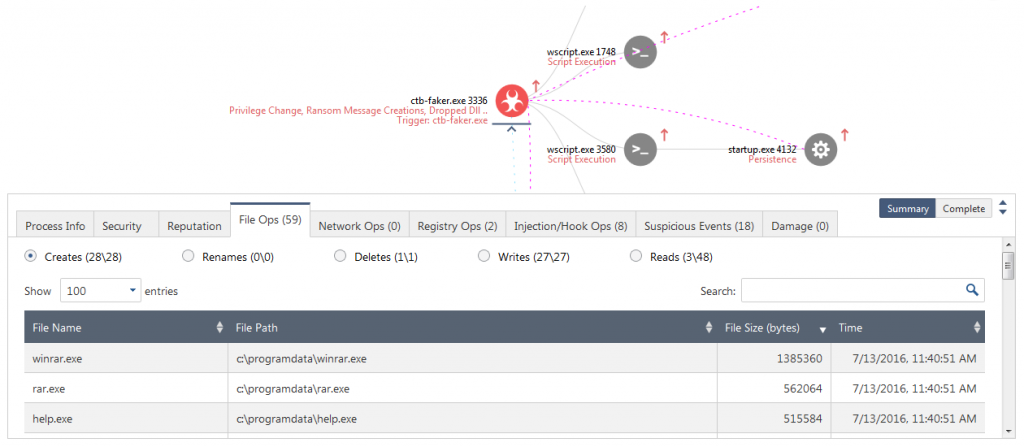



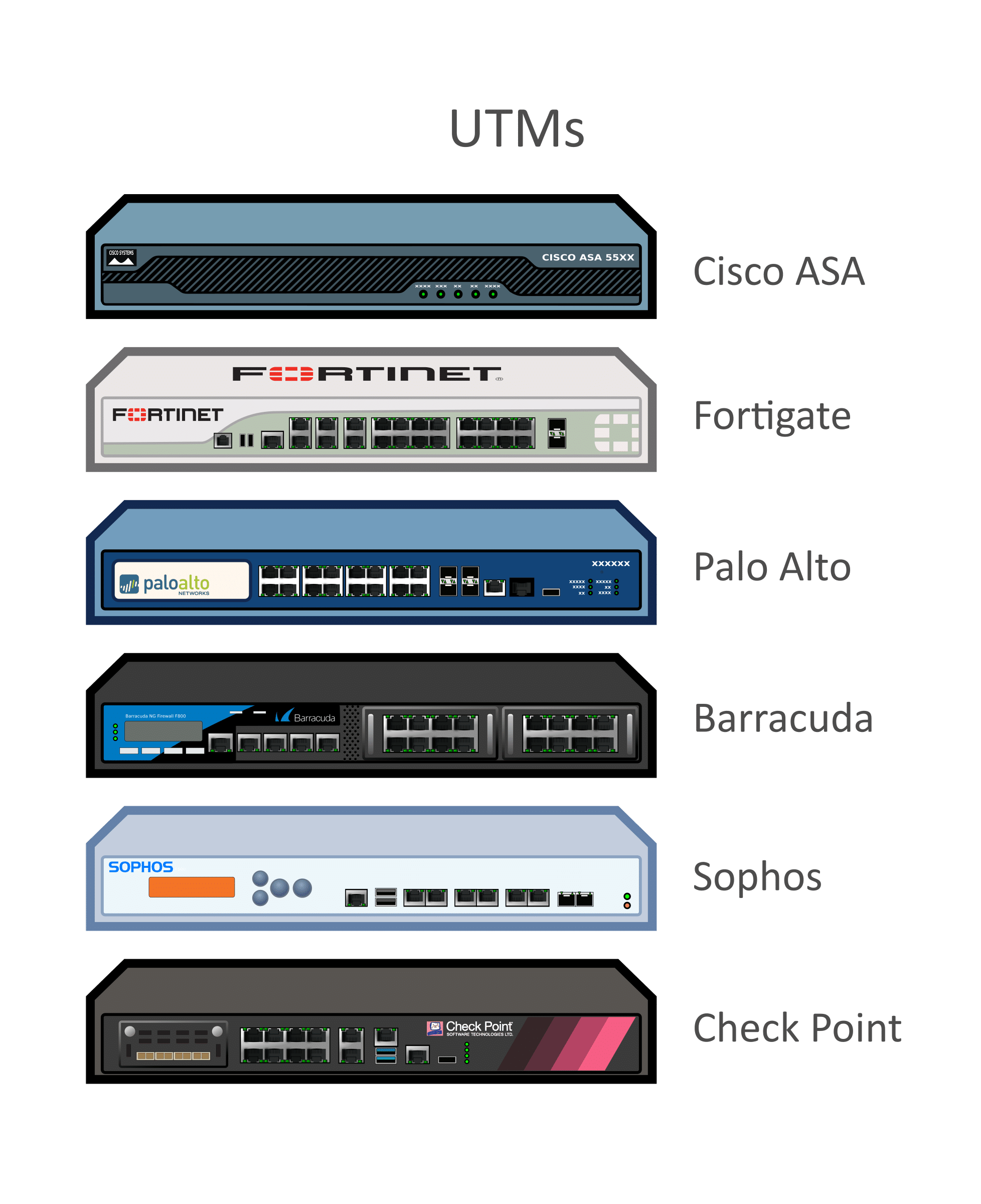



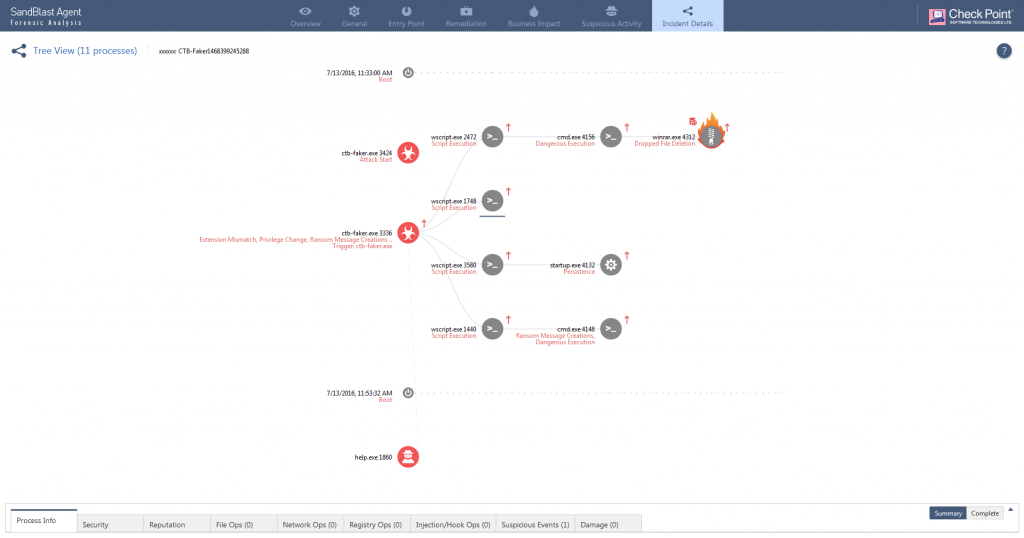
.jpg?width=1000&name=Cytomic_EDR(USE).jpg)